How To Run Fluxion Wifi Windows
./fluxion make sure that the fluxion folder has sufficient access rights and./fluxion file has executable permission. If not such a case just types this in the terminal chmod 755./fluxion. On the startup of this tool fluxion asks you to specify which WLAN interface do you use to hack WiFi. How to install Fluxion in Linux Mint or Ubuntu. Fluxion is a program to audit wireless Wi-Fi networks. It uses social engineering instead of brute-force. Fluxion is a successor of well-known linset. This guide will show installation process of Fluxion on Linux Mint or Ubuntu. The application has required dependencies.
Hello Friends.This is another tutorial in Cracking Wifi series.Today we are using another application named 'FLUXION'.NOTE: This video is for EDUCATIONAL PURPOSE only.The main advantage of fluxion is that it doesn't use any wordlist or perform bruteforce attack to break the key.Fluxion creates a Open twin Ap of the target network.When someone tries to connect to that network a fake authentication page pops up asking for key.When user enters the key, fluxion captures that key and provides us. Step 1: Download and Install Fluxion into Your System.Goto.
What is Fluxion for?is a security auditing and social-engineering research tool. It is a remake of linset by vk496 with (hopefully) less bugs and more functionality. The script attempts to retrieve the WPA/WPA2 key from a target access point by means of a social engineering (phishing) attack. It's compatible with the latest release of Kali (rolling).
Fluxion Tool
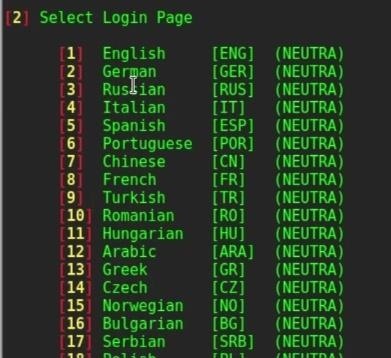
Fluxion's attacks' setup is mostly manual, but experimental auto-mode handles some of the attacks' setup parameters.The advantage of this approach is that it does not require a long-time brute-force on a powerful hardware. Sudo systemctl stop NetworkManagersudo airmon-ng check killTypical launch of the program, go to its folder:cd fluxion/The program is updated very often, so to download the latest version, run the command:git pullAnd we start:sudo./fluxion.shSelect language:We need to grab a handshake. It will not be used for brut-force (there will not be brut-force at all). But it is necessary to check if the user entered the correct password. Therefore, we select item two:2 Handshake Snopper Acquires WPA/WPA2 encryption hashes.Select a wireless interface for target searching:Select the channel where you want to search for targets:Five seconds after the target AP appears, close the FLUXION Scanner ( ctrl+c).When you see the desired target, close the new window, the list of access points will be displayed in the main program window.
When entering the number of an access point, which we will attack, DO NOT enter leading zeros.Select an interface for target tracking.Select a method of handshake retrieval1 Monitor (passive)2 aireplay-ng deauthentication (aggressive)3 mdk3 deauthentication (aggressive)A passive method of attack forces the radio to go completely silent, making the attack subtle (undetectable), and allowing for better listening. This method should work best for situations where the target is far away. The downside is the fact the radio must keep listening until someone connects to the target access point, which could take a very long time.An aggressive method of attack uses a deauthenticator, either aireplay-ng or mdk3, and sends deauthentication packets to the target access point's clients. This method is considered aggressive because it is essentially jamming the connection between the target access point and its clients, effectively cutting the connection between the two. Once the connection has been broken, some devices will automatically attempt to reconnect, sending a 4-way handshake which fluxion's radio could catch. This method could be considered illegal.
Make sure to follow governing laws applying to you. We're not liable for your irresponsibility.Select a method of verification for the hash. Here we select the program with which help it will be determined whether enough frames have already been captured to verify the password or not:How often should the verifier check for a handshake?How should verification occur?1 Asynchronously (fast systems only).2 Synchronously (recommended).This sets how verification occurs in relation to capturing data, either simultaneously (asynchronously), or back-to-back (synchronously).The asynchronous option will run the verifier while the computer is still capturing data.
This could cause an issue in slow systems, because pyrit stripLive might be interrupted by the captor overwriting data too early. The probability of encountering that problem increases over time, since more data needs to be examined by pyrit stripLive. I suggest avoiding this if possible, or to limit its use to places were the handshake file will be caught relatively quickly.The synchronous option will halt data capturing before attempting to check for a handshake, to prevent the issues described before. The downside of this method is the fact it'll stop listening while checking for handshakes, meaning it could miss a handshake while checking for one.Three additional windows will appear periodically.
If a handshake is captured, i.e. The attack succeeded, then one of the windows will have such an entry, and the other windows will be closed and the attack stopped:Now go to the Captive Portal attack.Many of the wireless adapters used in penetration testing support the addition of a virtual wireless interface.
This interface can be in monitor mode or in AP mode. Due to this possibility, when creating a fake access point and simultaneously jamming a real access point, you can use one single Wi-Fi card. And Fluxion knows how to do it.But since the fourth version, Fluxion has added one more function - to follow the attacked access point. The problem is that some access points, when a deauthentication attack is conducted against them, change the channel on which they operate. As a result, they become immune to our attack, you have to stop Fluxion, re-select the target and launch the attack again.
The essence of the new function is that Fluxion regularly checks which channel the access point is operating on, and if it changes the channel, Fluxion automatically restarts the attack on the correct channel.So, if you want to use the pursuit function, then you need a second wireless card, which supports monitor mode. If you do not have one, you can skip using this function.We launch the another attack:1 Captive Portal Creates an 'evil twin' access point.Fluxion is targetting the access point above.
Now choose the interface for jamming ( choose a different one than the one chosen for the pursuit, otherwise there will be problems):Select an interface for the access point. If you do not have a separate wireless card to create an access point, then select the same interface that is selected for jamming (this is normal and if the wireless card supports adding a virtual interface, everything will work fine):Select the program that will create the access point. The authors recommend avoiding airbase-ng if you use the same Wi-Fi card both for creating an access point and for deauthentication (jamming):If you have already captured a handshake, a message will appear that it has been found.
You can use it or specify a path to another:Again select a method of verification for the hash:Next, we select the source of the SSL certificate for the captive portal. Options:1 Create an SSL certificate2 Detect SSL certificate (search again)3 None (disable SSL)When prompted, select an SSL certificate source for the captive portal, or select to disable SSL.SSL is a method of encryption used to establish a secure connection between two points. In this case, the two points are the captive portal’s web server, and the target client.If you've got a personal certificate, you must save it at fluxion/attacks/Captive Portal/certificate/server.pem and the attack will automatically detect it and auto-select it.If you don't have a personal certificate, you may select to automatically generate one. The downside is that the certificate, having been created by a random individual, will not be trusted by any device, which will likely trigger warnings for clients attempting a secure connection to the captive portal.If you would rather not bother with SSL, you can choose to disable it. Once disabled, the captive portal’s web server will only accept unencrypted connections, which exposes the information clients send to fluxion. This can be particularly unsafe if someone’s spying on network traffic.
